
Even a computer would need some time to endure 1000s of phrases, but with hashing, all it takes is comparing a couple of people to find out whether two sets of data are unique.
This system establishes an index or location for that storage of an item in a data construction. It might not be strictly relevant to essential-price pairs only In case you are manipulating the d
Abide by Hashing refers to the whole process of producing a set-sizing output from an enter of variable dimension using the mathematical formulation often called hash capabilities. This method establishes an index or area for your storage of the product in a data composition.
In the event the marijuana plant is smoked, it leaves driving a thick black resin on pipes. That resin might be scraped off and smoked, even though it does not contain as powerful a dose of THC as pure hash. Benefits
Information integrity. Hashing is commonly employed to guarantee info integrity. By building a hash value for an level of info, such as a file or information, a user can later Evaluate it with the hash value of the received info to verify if any improvements or corruption happened during transmission.
Hashing is a way used in facts buildings that successfully merchants and retrieves knowledge in a way which allows for speedy entry.
Unlike chaining, open addressing doesn't retailer several components into the same slot. Below, Just about every slot is both stuffed with one essential or remaining NIL.
When the principal goal of hashing is just to detect mistakes and modifications in details, then most of the people work with a cyclic redundancy Test (CRC) code. Hashing with CRC32 is usually a quick and easy way to check file integrity, notably with ZIP documents and data files downloaded from FTP servers.
As soon as the password entropy may be the same given that the possible entropy of your respective hashes, adding more people is pointless, it would not strengthen the standard of the password. Alternatively, telling a consumer that their password is too extensive is additionally pretty inconvenient.
$begingroup$ Disregarding that incontrovertible fact that passphrases are salted, and assuming that you'll be looking for your collision with a single distinct person.
Databases management. When working with massive data sets, combing by means of numerous entries to obtain the check here mandatory info can be intimidating. Hashing provides an alternative by permitting buyers try to find information documents using a search essential in addition to a hash function alternatively than an index structure.
M*A*S*H could be the best Television sequence at any time made, it's really made an impression. Using black humour have to have been the only method of getting from the working day for most troopers, and it gave me an 1 gram hash notion of how awful the war have to have been. Definitely a terrific Television series filled with humour and jokes that makes you chuckle each time.
Essential: A Critical is often something string or integer and that is fed as input while in the hash perform the system that decides an index or locale for storage of the item in a data construction.
In North The us, hash is also known as “resin,” and some drug people cultivate it from drug paraphernalia.
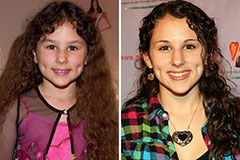 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now!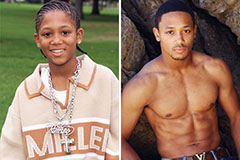 Romeo Miller Then & Now!
Romeo Miller Then & Now! Katie Holmes Then & Now!
Katie Holmes Then & Now! Lynda Carter Then & Now!
Lynda Carter Then & Now! Stephen Hawking Then & Now!
Stephen Hawking Then & Now!